News

WDK 10.0.26100.0 GDT for Ghidra 12
WDK 10.0.26100.0 GDT for Ghidra 12 using clang preprocessing and sanitization so Ghidra’s parser accepts all kernel/CRT prototypes. Coming from IDA Pro that does this automatically, in Ghidra is not...
WDK 10.0.26100.0 GDT for Ghidra 12
WDK 10.0.26100.0 GDT for Ghidra 12 using clang preprocessing and sanitization so Ghidra’s parser accepts all kernel/CRT prototypes. Coming from IDA Pro that does this automatically, in Ghidra is not...
![[Video] Juan Sacco, founder of Exploit Pack at No Hat conference (Italy)](http://www.exploitpack.com/cdn/shop/articles/Screenshot_2025-12-22_173719_845038cb-29e2-49e4-a01a-52b0b00d4240.png?v=1766421604&width=533)
[Video] Juan Sacco, founder of Exploit Pack at ...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop focused on three primary exploit...
[Video] Juan Sacco, founder of Exploit Pack at ...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop focused on three primary exploit...
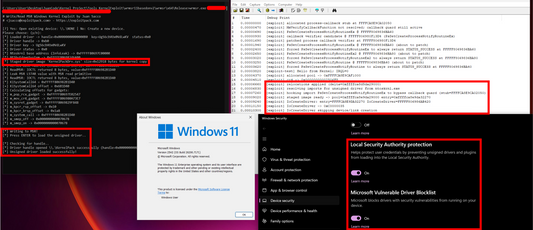
Unsigned drivers loading on Windows 11 25H2 (fu...
After having developed working exploits for physical r/w (ZwMapViewOfSection) and r/w through MSR (L_STAR) for Windows 11 25H2, I decided it was time to take it up a notch and...
Unsigned drivers loading on Windows 11 25H2 (fu...
After having developed working exploits for physical r/w (ZwMapViewOfSection) and r/w through MSR (L_STAR) for Windows 11 25H2, I decided it was time to take it up a notch and...

Juan Sacco, founder of Exploit Pack at No Hat c...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop was strictly technical: practical tools...
Juan Sacco, founder of Exploit Pack at No Hat c...
Juan Sacco from Exploit Pack delivered a focused, hands-on workshop titled “Subverting the Windows Kernel with rootkits and exploits” at No Hat in Italy. The workshop was strictly technical: practical tools...
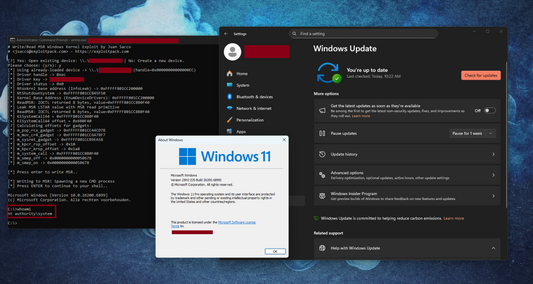
0-Day MSR Kernel Exploit for Windows 11 25H2
New 0-day Windows Kernel Exploit, working in Windows 11 25h2 fully patched.It took me 2 weeks of endless coffee cups! MSRs control where the CPU jumps for privileged transitions, they...
0-Day MSR Kernel Exploit for Windows 11 25H2
New 0-day Windows Kernel Exploit, working in Windows 11 25h2 fully patched.It took me 2 weeks of endless coffee cups! MSRs control where the CPU jumps for privileged transitions, they...

Driver Buddy Revolutions for IDA
Driver Buddy Revolutions is an IDA Pro plugin that automates common Windows kernel driver research. Author: Juan Sacco What it does: 1. IOCTL enumeration and scoring Scans the driver’s code...
Driver Buddy Revolutions for IDA
Driver Buddy Revolutions is an IDA Pro plugin that automates common Windows kernel driver research. Author: Juan Sacco What it does: 1. IOCTL enumeration and scoring Scans the driver’s code...
