Exploit Pack
Control Pack Black Friday Deal
Control Pack Black Friday Deal
Control Pack gives you full access to the most advanced and stealthiest post-exploitation C2 framework. It includes multi-platform agents built for stealth, with EDR/AV evasion at their core, using the latest techniques to bypass modern antivirus (AV) and endpoint detection and response (EDR) systems with ease. Your license also comes with technical support and live online training for you and your team.
Black Friday Deal: This lifetime license grants a single individual permanent access to our tools (Exploit Pack, Control Pack, or Kernel Pack) for personal, non-commercial research and educational use only.
Personal (individual) license only. Licenses are sold to individual persons and are not available for purchase by companies, organisations, or teams. If you need multiple seats or a corporate/bulk license, please contact support@exploitpack.com.
Research & educational use only. Licenses are issued for personal research, security testing in authorised environments, and academic use. Commercial use, resale, redelivery or use to provide services to third parties is strictly prohibited.
Single‑user, single machine. Each license is watermarked and tied to the email used at purchase; one license per person, one machine per license.
Sanctions & export compliance. We do not sell to countries subject to EU bans or sanctions. By completing purchase you confirm you are not located in, nor a resident of, any EU‑banned or sanctioned country.
Legal & ethical responsibility. It is the purchaser’s responsibility to ensure all use of these tools complies with local laws and the policies of any systems being tested. You must have explicit authorization before testing third‑party systems.
Couldn't load pickup availability
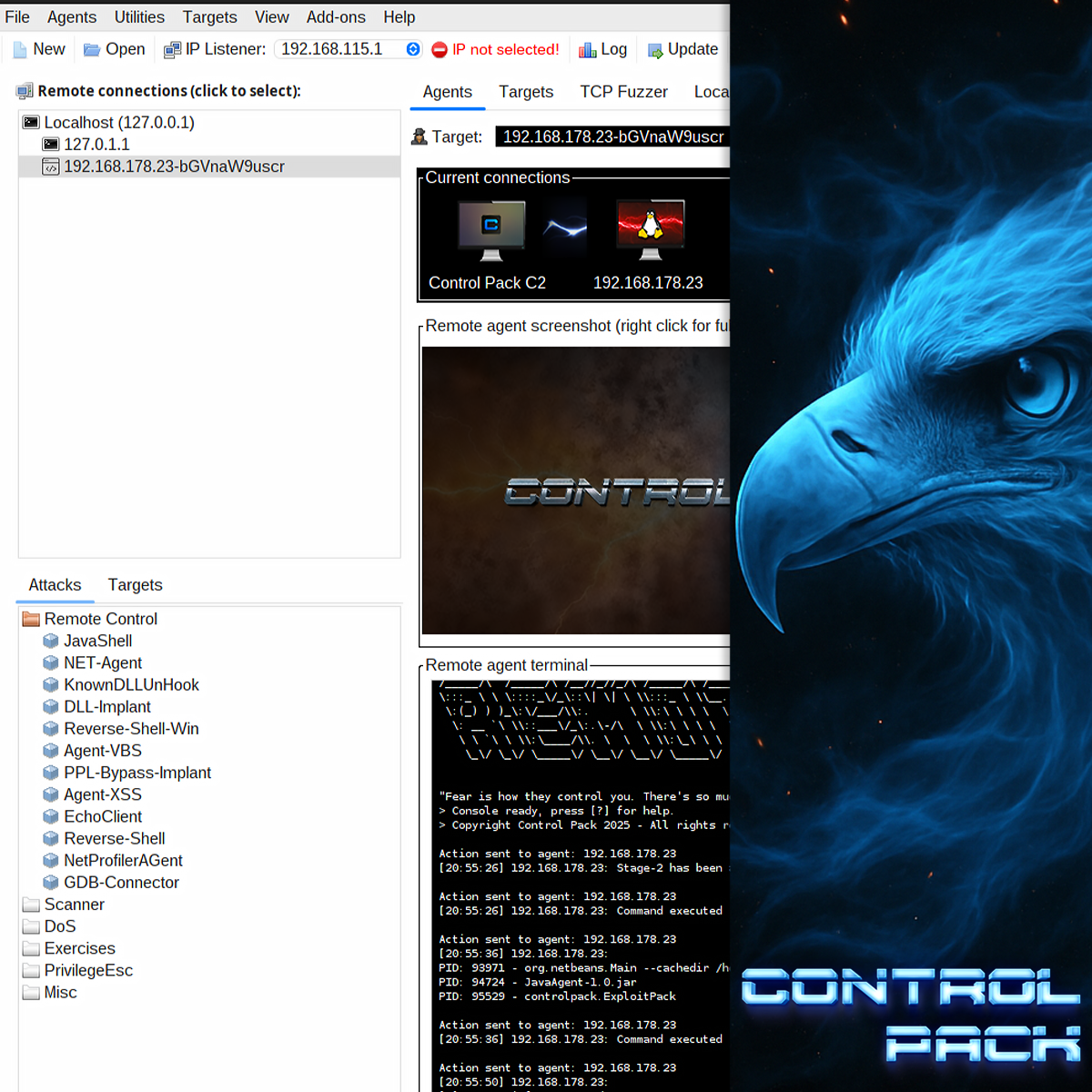
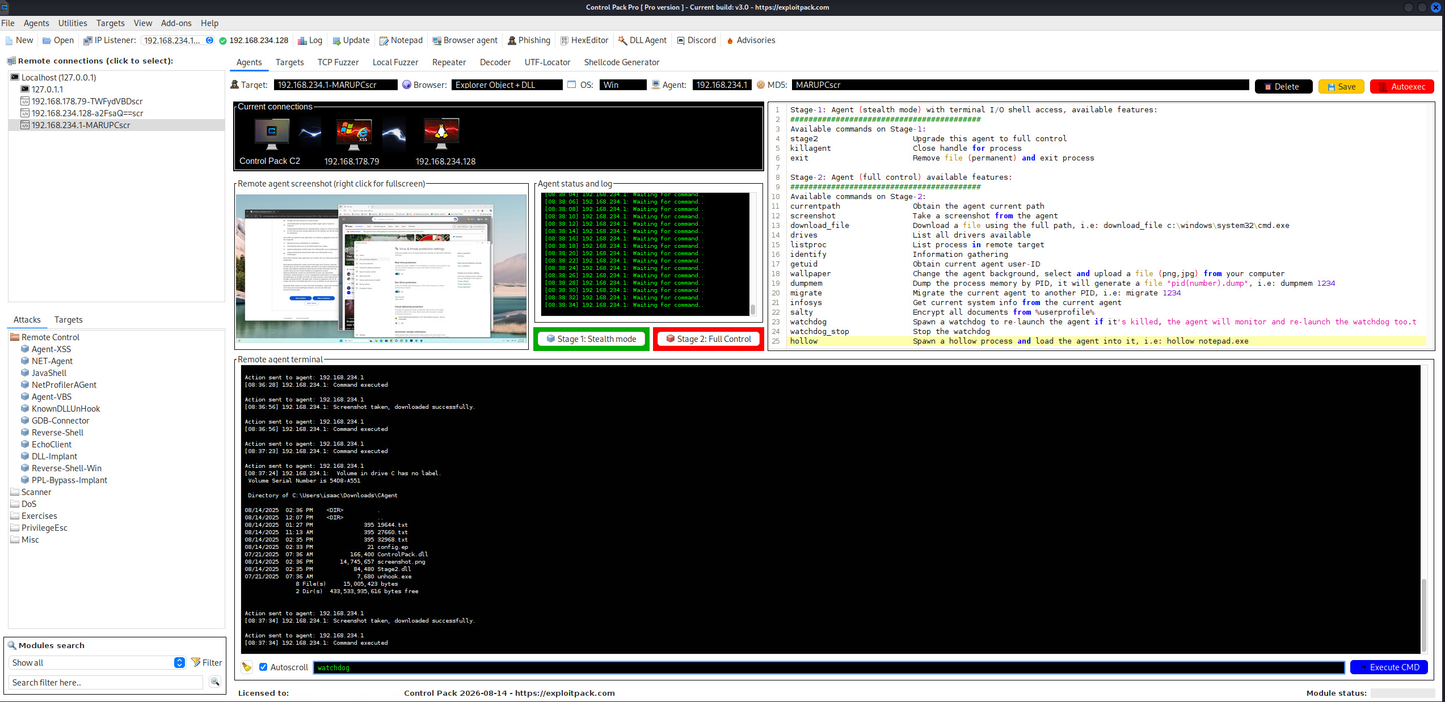
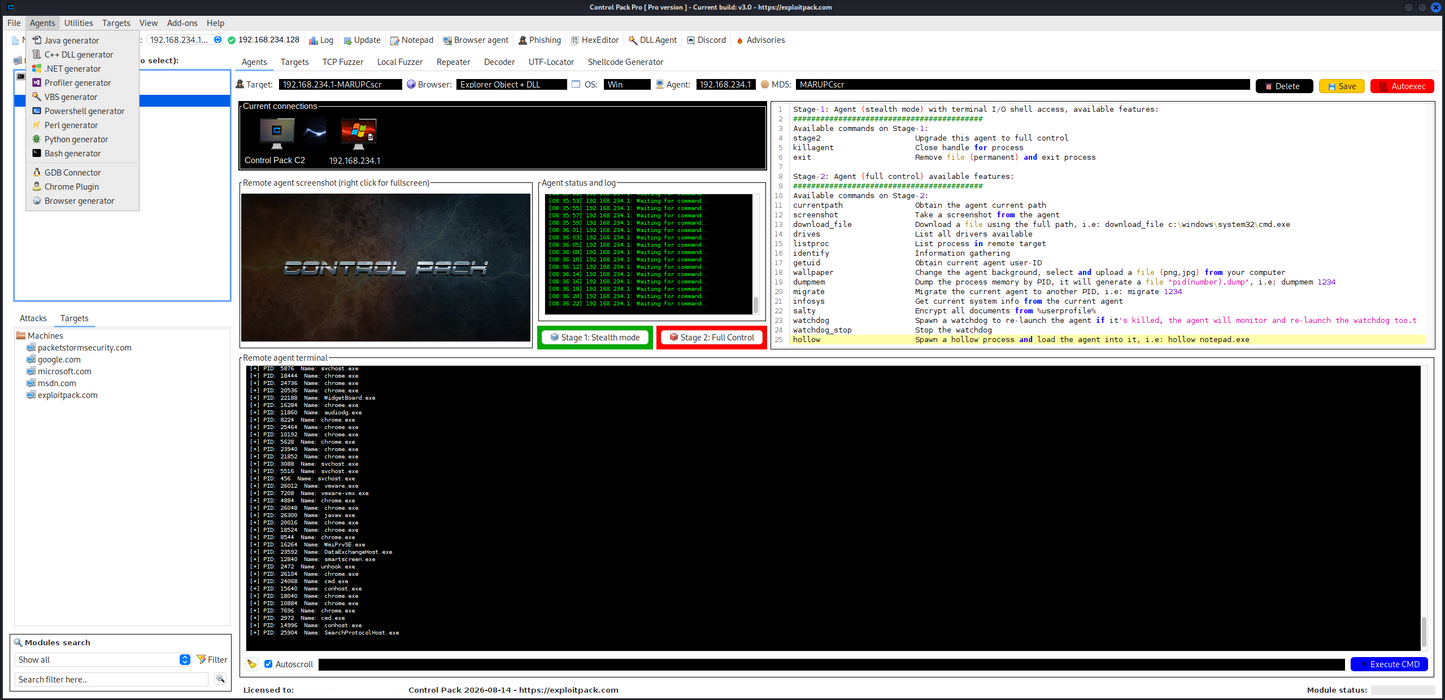
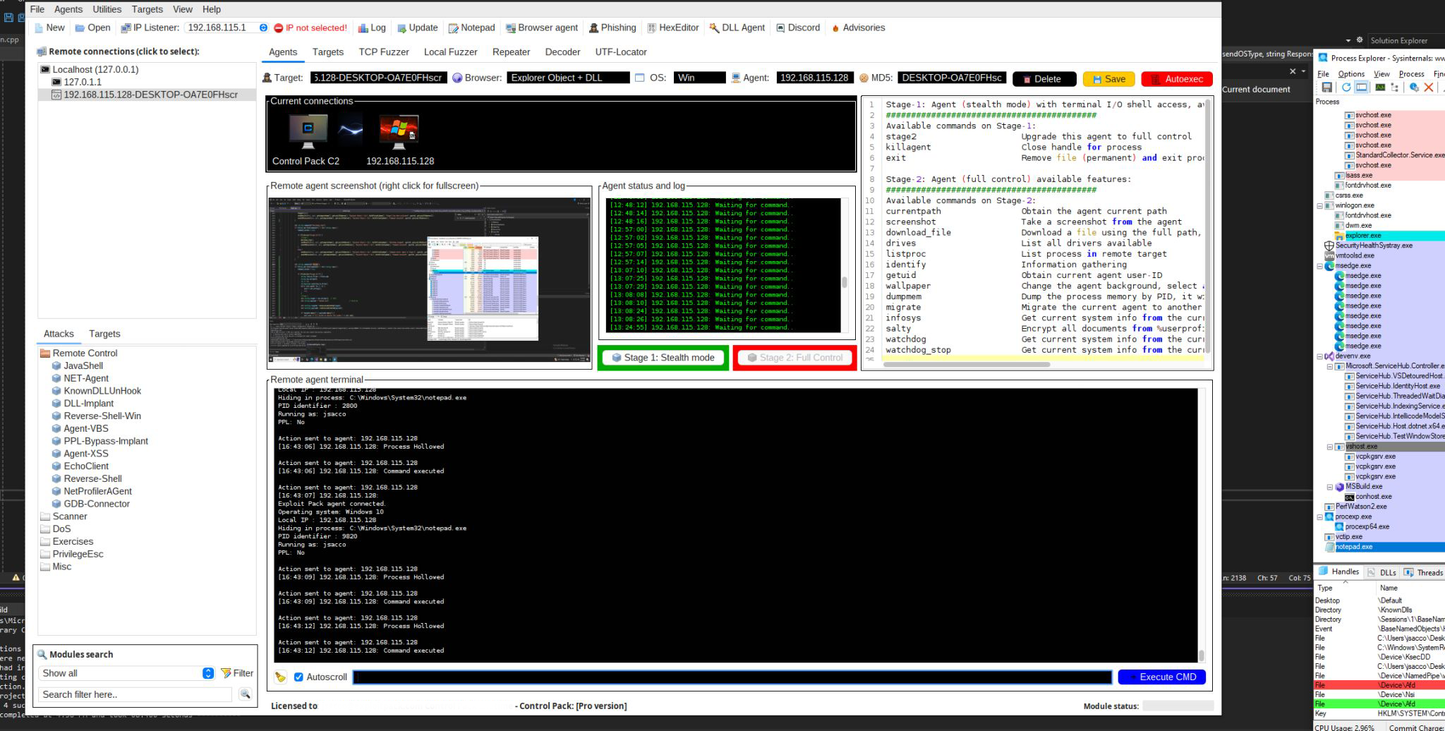
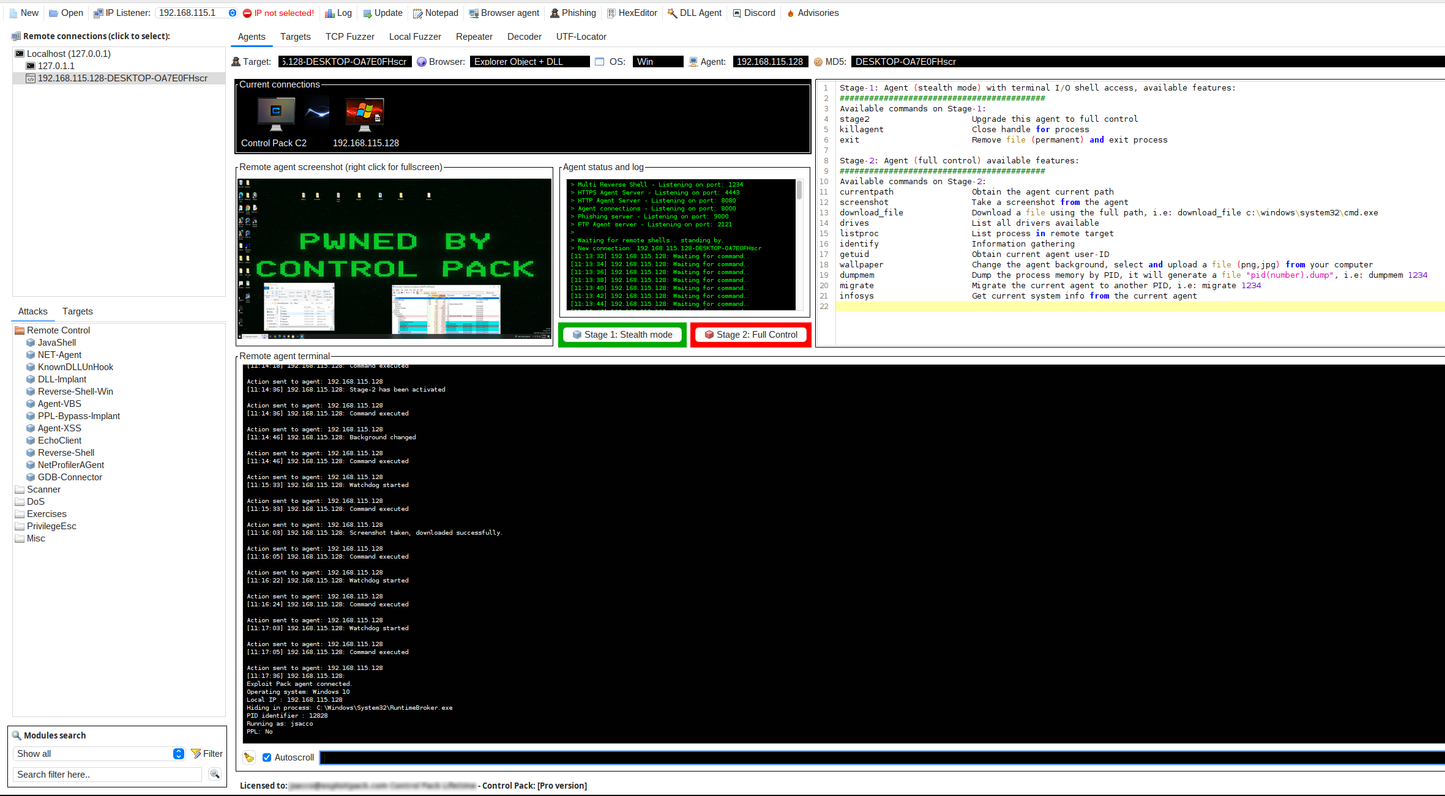
Control Pack C2. Evasion and bypass in userland.
Control Pack provides a full-featured C2 framework for Red Teams and cybersecurity professionals.
Deploy and manage agents, simulate attacks, test AV/EDR detection and evasion, execute remote commands, and maintain persistence across multiple environments.
Control Pack features an easy-to-use graphical interface that gets you running quickly, along with modular, customizable agents tailored to the needs of a specific target or engagement.
Do you need a quote? Contact us
-

Control Pack works in two stages. Stage 1 gives you minimal terminal access. Once the agent moves to Stage 2, all functions are enabled. Using agents in stages helps avoid detection and forensic analysis in the event that the sample is captured.
-

Control Pack uses NTDLL Undocumented Functions, Direct Syscalls and removes hooks placed by AVs or EDRs, and reloads their counterparts from disk, making it the quietest commercial C2 available in the market.
-

The Watchdog monitors a Control Pack agent in real time. If the agent stops due to user action, or by a security process, the Watchdog immediately launches a new instance. This ensures continuity against tampering or termination.
-

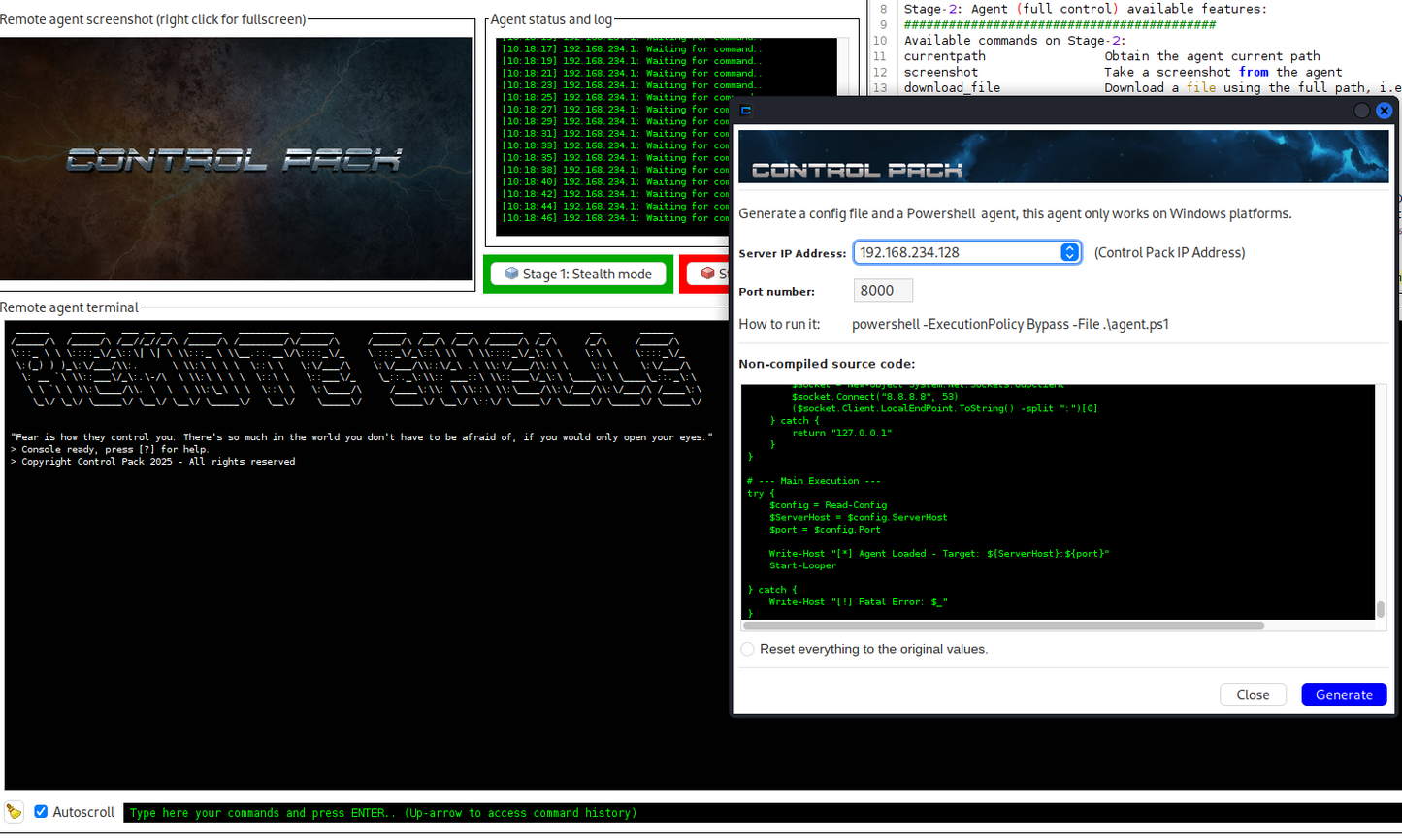
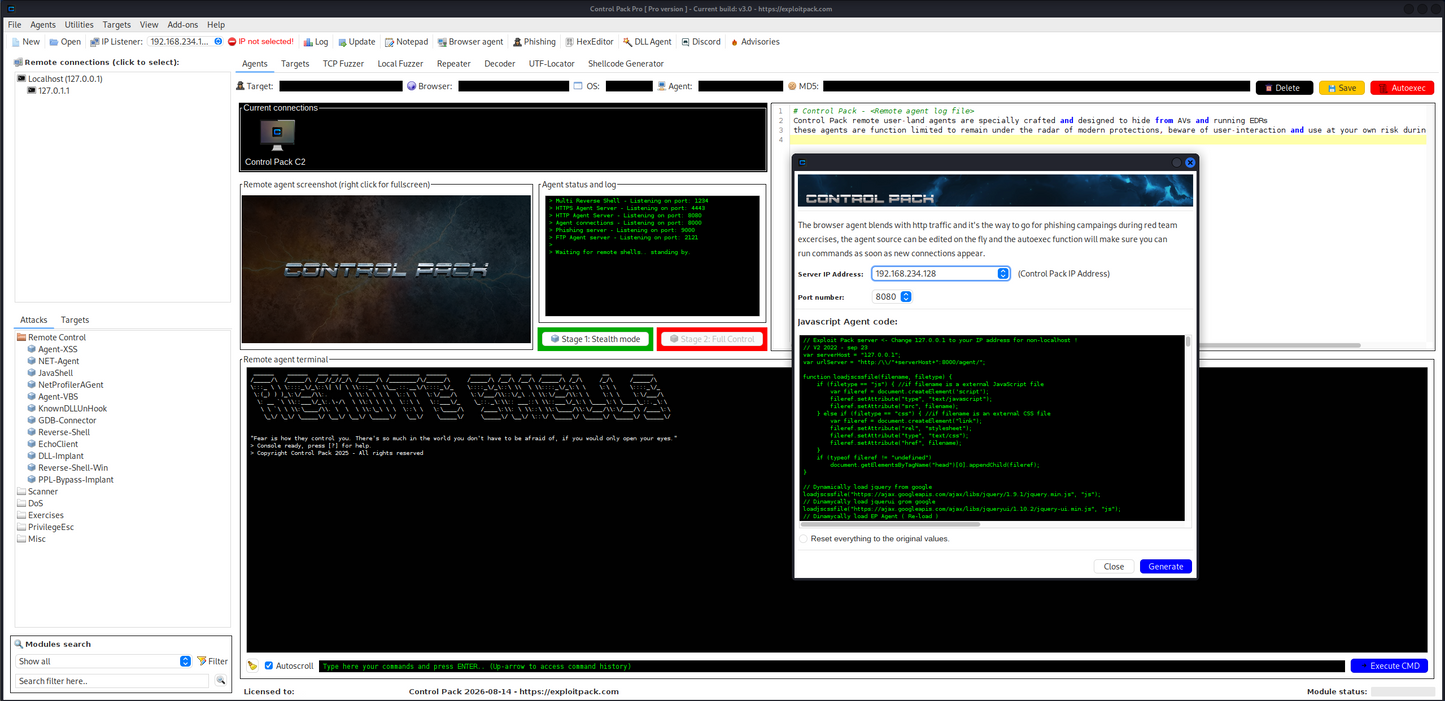
Multi-platform support: Java, C++, .NET, VBS, PowerShell, Perl, Python, Bash and browsers. Deploy and control payloads across multiple environments during Red Team exercises.
-

Control Pack agents offer functionalities for insight, control, and persistence: capture screenshots, transfer files, migrate processes, move laterally, and more (check documentation)
-

Never get stuck, your license includes technical support and consultation during your next project. We are here to help you achieve results and improve your Red Teaming capabilities.
Questions About This Product
What type of license is included?
All our tools are provided under an annual license.
Do licenses renew automatically?
No. Licenses are not automatically renewed. You may choose to renew each year at your own convenience.
List of features
✔ Regular monthly updates to keep you ahead with the latest techniques
✔ Ransomware ( DLL-Based ) for Red Team operations.
✔ DLL agent.
✔ .Net-Core agent.
✔ .Net Profiler agent.
✔ Python agent.
✔ In-memory agent.
✔ VBS-based agent (macros)
✔ Browser-based agent for XSS/Web attacks.
✔ Phishing campaigns.
✔ WebKit-based (Chrome) plugin agent.
✔ Auto execution of commands for new connections.
✔ Simple reverse shells, scalable to full agents.
✔ KnownDLL unhook for evasion and AV bypasses.
✔ Protected Process Light (PPL) ready agent for AV bypass.
✔ Persistence methods.
✔ GDB Connector for debugging.
✔ IDA Pro Connector for debugging.
✔ Antireversing techniques for agent protection.
✔ Technical support.
How many users can use one license?
Each license is issued on a single-user basis. Sharing between multiple individuals is not permitted.
Integration with other tools
Control Pack agents act as the middle layer: they receive payloads from Exploit Pack and provide a controlled execution environment for follow-on actions. From there, you can optionally escalate capabilities through Kernel Pack for deep-level persistence and complex post-exploit tasks.
Can I use the license against multiple targets?
Yes. While some tools in the industry restrict you to a limited number of targets, our licenses allow you to use the tool against as many machines as needed within your authorised engagements.
Delivery of licenses
Licenses are delivered digitally to the email used at purchase. Since they are sent manually, delivery may take up to 24 hours (usually faster).
Once the order is confirmed and the license has been delivered, it cannot be transferred, and refunds will not be issued.













